| Risk
and Vulnerability Assessment
A Risk Assessment identifies the
potential threat events and linked risks an organization
may be facing. The process requires an analysis of
historical data of security or criminal incidents which
may have taken place on or near the facility or location
under consideration. Available intelligence and
probability of crime assessments may also be used to
define the threat and risk environment. Added to this
is the assessorís industry knowledge and experience over
a range of environments which may have similarities with
respect to threats, risks and impacts.
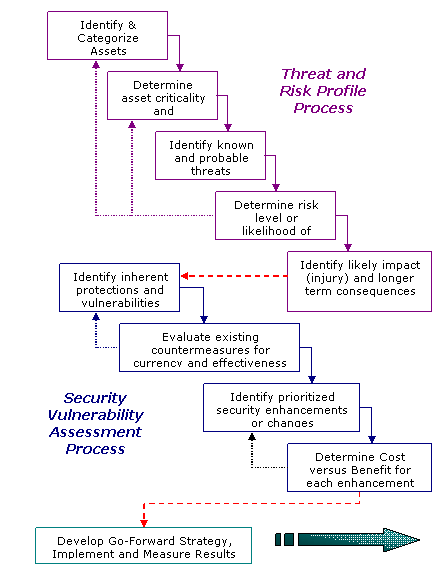
A threat and risk
assessment normally precedes a security vulnerability
assessment which identifies security vulnerabilities or
weaknesses existing at the facility or location(s) where
business is conducted. A criticality and prioritization
analysis for mission crucial assets forms part of the
vulnerability assessment and facilitates definition of
where security remedies are most needed. Processes such
as Pair-Wise Assessment and Pareto Analysis are often
used for this purpose. The figure below details some
common steps for both the risk and vulnerability
assessment processes.
Our
reporting addresses the vulnerabilities and how best
they might be addressed in a practical manner. We
provide prioritized recommendations and an
implementation plan focused on strategically improving
the security of the site and the safety of the
individuals who work or visit there.
To provide clients with a
structured process for tracking and completion of
security recommendations TBG often uses the SecureAssess
data collection and analysis tool which automates the
collection, collation, reporting and follow-up
information in a consistent manner for each site or
facility.
This process also
facilitates the selection of security compliance levels,
which may be stipulated by regulation or corporate
polity and automatically reports when specific areas of
security fall below the target levels. |